Windows Server 2008 R2 Unleashed (207 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto
OU that contains a computer on which the printer can be installed.
14. Reboot the computer to which the DeployPrinterGPO applies.
15. After reboot, log on and verify that the printer was successfully installed. If the
printer was not installed, the system might require an additional reboot or
Synchronous Foreground Group Policy Processing might need to be enabled.
16. After the GPO testing is complete, log back on to the Windows Server 2008 R2 sys-
tem, open the GPMC, and link the DeployPrinterGPO to the necessary OUs.
Deploying printers using GPOs to users follows mostly the same process; except when
deploying the printer, the check box to deploy in the user section should be checked and
instead of a computer startup script a user logon script should be defined. Deploying
printers using GPOs for computers or users simplifies the installation and removal of
printers but does not set the default printer if multiple printers are installed on the
computer or in the user profile. Setting the default printer should be performed by the
1058
CHAPTER 27
Group Policy Management for Network Clients
end user, or the new Printer settings available in the User Configuration Preferences node
can be used to install and set the default printer.
Mapping Drives Using Preferences User Drive Maps Extension
Using the new Preferences User Drive Maps extension in domain policies, administrators
can now map network drives for end users without scripts. To define a mapped drive for a
user using the Preferences User Drive Maps extension in a domain policy, perform the
following steps:
1. Log on to a designated Windows Server 2008 R2 administrative server.
2. If necessary, install the Group Policy Management Console on the system, as
detailed previously in this chapter.
3. After the tools are installed, click Start, click All Programs, click Administrative Tools,
and select Group Policy Management.
4. Add the necessary domains to the GPMC, as required.
5. Expand the Domains node to reveal the Group Policy Objects container.
6. Create a new GPO called UserDriveMapGPO.
7. Open the GPO for editing and, in the Group Policy Management Editor window,
select and expand the User Configuration node in the tree pane.
ptg
8. In the tree pane, expand the Preferences node and the Windows Settings node.
9. Select the Drive Maps preference setting, right-click the setting and select New –
Mapped Drive.
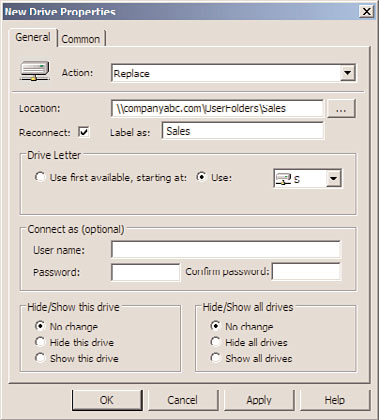
10. When the New Drive Properties window opens, select the Replace action from
Actions pull-down menu.
11. Type in the location of the network share that will be mapped to a drive letter with
this setting. For this example, we will use \\companyabc.com\UserFolders\Sales.
12. In the Drive Letter section, select the Use option button and select the desired drive
letter by choosing it from the pull-down menu. For this example, select the S drive.
13. Check the Reconnect check box to reconnect the Drive Map, enter the Label as Sales,
and click OK to complete the creation of the Drive Map setting item, as shown in
Figure 27.12.
14. Close the Group Policy Management Editor.
15. In the Group Policy Management Console, link the GPO to the desired domain, site,
or organizational unit that contains a user account for testing.
16. Test the new policy and when the policy delivers the desired results, create the nec-
essary GPO links from the administrative server, close the Group Policy Management
Console window, and log off of the server.
Configuring Preference Item-Level Targeting
There are many instances in group policy deployments when an administrator desires to
apply a particular preference setting to only a subset of computers or users. When this is
the case, Preference Item-Level Targeting can be used. For example, a Group Policy admin-
Managing Computers with Domain Policies
1059
FIGURE 27.12
Configuring a new Drive Map GPO Preference item.
ptg
istrator can create a single domain policy named UserDriveMapGPO and leave the policy
filtering set to authenticated users, and it can be linked to the domain. In this case, if a
Drive Map preference is defined, all users in the domain will map the same drive. Now
within this single policy, several Drive Maps can be created but each Drive Map can be
applied to only specified users or security groups using item-level targeting with the Drive
Map preference options. The following steps detail segmenting the application of a Drive
27
Map setting to a security group using item-level targeting:
1. Log on to a designated Windows Server 2008 R2 administrative server used to create
the UserDriveMapGPO, as detailed in the previous section.
2. Click Start, All Programs, Administrative Tools, and select Group Policy
Management.
3. Add the necessary domains to the GPMC, as required.
4. Expand the Domains node to reveal the Group Policy Objects container.
5. Select the UserDriveMapGPO and open it for editing.
6. In the Group Policy Management Editor window, select and expand the User
Configuration node in the tree pane, and expand the Preferences node and
Windows Settings node.
7. Select the Drive Maps preference setting in the tree pane and locate the S drive map
in the Settings pane that was previously created.
8. Right-click the S drive map and select Properties.
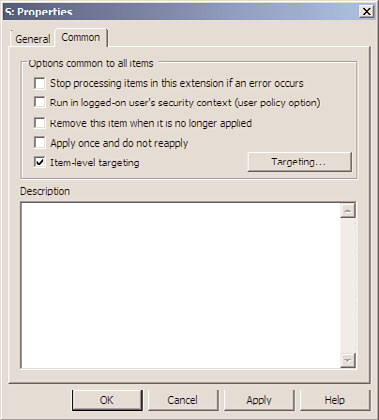
9. Select the Common tab and check the Item-Level Targeting check box, as shown in
Figure 27.13.
1060
CHAPTER 27
Group Policy Management for Network Clients
FIGURE 27.13
Enabling item-level targeting for a GPO Preference setting.
ptg
10. Click the Targeting button to open the Targeting Editor.
11. In the Targeting Editor window, click the arrow in the New Item pull-down menu to
reveal each of the different options that can be used for item-level targeting and
select Security Group.
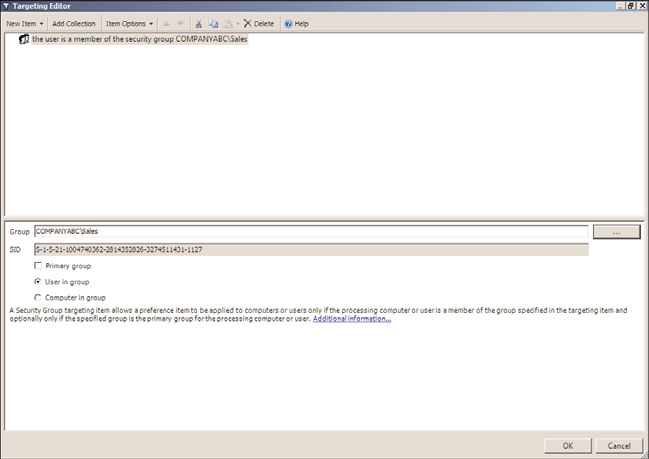
12. When the security group item is added to the window, click the “...” button to
locate and add a security group from the domain, as shown in Figure 27.14; for this
example, it is the companyabc\sales security group.
13. Click OK when completed and close the Group Policy Management Editor.
14. Test the application of the policy on a test system with a test user account in the
sales group to verify that the desired functionality is being delivered.
Configuring Remote Desktop and Remote Administration Support
A common Group Policy request from IT administrators who need to support Windows
XP, Windows Server 2003, Windows Vista, Windows 7, Windows Server 2008, and
Windows Server 2008 R2 systems with the Windows Firewall enabled is to allow for
remote administration. Group Policy can manage this task with minimal configuration. To
enable Remote Desktop on Windows XP, Windows 2003, Windows Vista, or Windows
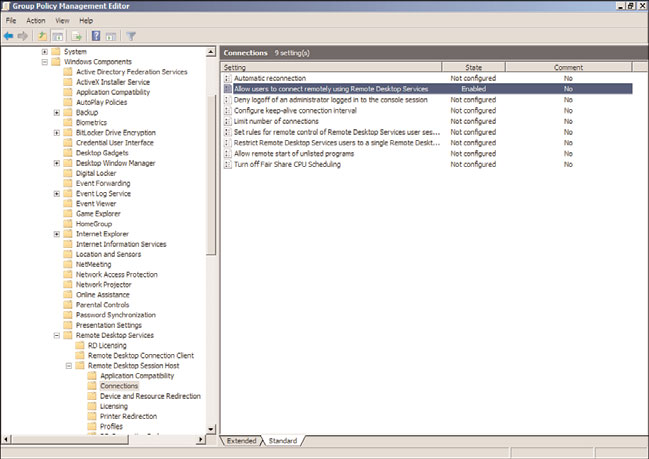
Server 2008 systems, enable the Allow Users to Connect Remotely Using Remote Desktop
Services setting. This setting is located in Computer Configuration\Policies\
Administrative Templates\Windows Components\Remote Desktop Session Host\
Connections node, as shown in Figure 27.15. When this GPO is saved and linked to a
GPO with computers in it, all the computers will have Remote Desktop enabled.
By default, only members of the Administrators group will be able to connect using
Managing Computers with Domain Policies
1061
Remote Desktop. If this needs to be changed, additional users can be added to the local
Remote Desktop Users group.
ptg
FIGURE 27.14
Specifying the companyabc\sales security group as an item-level target for a
GPO Preference setting.
27
FIGURE 27.15
Enabling Remote Desktop using a GPO.
1062
CHAPTER 27
Group Policy Management for Network Clients
After Remote Desktop is enabled on a system, the firewall exceptions still need to be
configured—otherwise, Remote Desktop is not possible. Remote Desktop is a built-in
exception in the Windows XP, Windows Vista, Windows 7, Windows Server 2003,
Windows Server 2008, and Windows Server 2008 R2 basic firewall. In addition, remote
administration is a built-in exception; to configure these exceptions, see the following
section, “Configuring Basic Firewall Settings with Group Policy.”
Configuring Basic Firewall Settings with Group Policy
In many organizations, part of the responsibility of supporting end users requires the
ability to remotely manage the desktop. Many organizations leverage the built-in
Windows tools for remote management, whereas many others utilize third-party products.
Remote management tasks of workstations can include installing custom software for a
particular user or group of users, manually running Windows Update, assisting with the
installation of local printers, adding local user accounts, changing local group member-
ship, or troubleshooting reported issues.
The Microsoft Windows Firewall includes multiple firewall profiles that contain separate
firewall rules and firewall exceptions. Windows XP and Windows Server 2003 contain a
domain and standard firewall profile. The domain profile is activated when the desktop is
ptg
on the same network as a domain controller. The standard profile is activated when the
desktop is on a remote or public network, or in many cases, if the machine is connected
to a VPN that does not support proper communication, it might also remain in the stan-
dard firewall profile. Windows Vista, Windows 7, Windows Server 2008, and Windows