Windows Server 2008 R2 Unleashed (69 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto
Secure DNS with DNSSEC
321
FIGURE 10.33
Encrypted zone records.
ptg
There are four records for each previous entry now, which are the following:
. Standard A Record
. RR Signature (RRSIG) Record for the Standard Record
. Next Secure (NSEC) Record
. RR Signature (RRSIG) Record for the Next Secure Record
Without any additional configuration, the DNS clients blissfully ignore the DNSSEC for
the zone. To have the clients use the DNSSEC properties of the DNS zone, they must be
configured to request secure DNS entries. This is done by configuring a Name Resolution
Policy Table (NRPT) policy for clients.
The NRPT policy can be configured through group policy. The steps to create a NRPT
group policy for the secure.companyabc.com zone are the following:
1. On the domain controller DC1, launch Server Manager.
10
2. Expand Features, Group Policy Management, Forest: companyabc.com, Domains,
and select companyabc.com.
3. Right-click on companyabc.com and select Create a GPO in This Domain, and
Link It Here.
4. Enter NRPT Group Policy Object and click OK.
5. Right-click the NRPT Group Policy Object link and select Edit.
6. Expand Policies, Windows Settings, and select Name Resolution Policy.
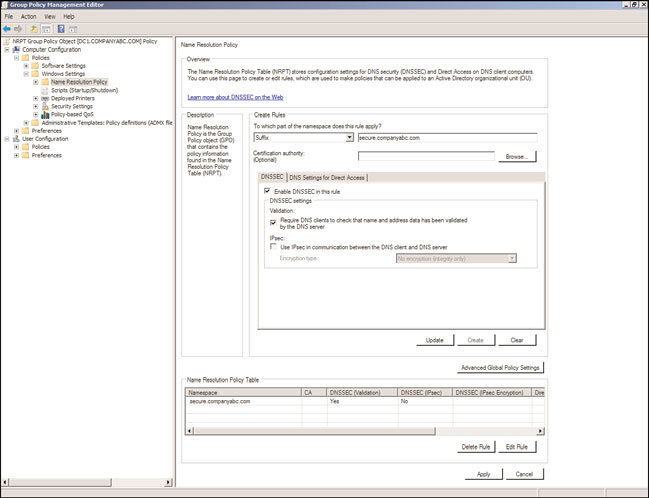
322
CHAPTER 10
Domain Name System and IPv6
7. In the field “To which part of the namespace does this rule apply?” select Suffix and
enter secure.companyabc.com.
8. In the DNSSEC tab, check the Enable DNSSEC in This Rule.
9. Check the Validation box Require DNS Clients to Check That Name and Address
Data Has Been Validated.
NOTE
The wording of this option is precise. The Windows DNS client will check that the DNS
server has validated the data, but will NOT do the validation itself.
10. Click the Create button to create the record in the Name Resolution Policy Table at
the bottom of the screen. Figure 10.34 shows how the record should look.
ptg
FIGURE 10.34
Name resolution policy.
11. Close the GPMC editor to save the changes.
Now, all domain DNS clients will request that DNS servers check the validity of the
lookups for domain secure.companyabc.com using DNSSEC.
Additional steps that might be needed to maintain the secured DNS zone include the
following:
Best Practices
323
. Back up the KSK and ZSK certificates.
. Back up the secured and unsecured zone files.
. Establish a maintenance schedule to refresh the zone signatures.
DNS has proven itself over time to be a robust, dependable, and extremely scalable solu-
tion to name resolution. Windows Server 2008 R2 takes DNS to the next level and builds
on the enhancements introduced with Windows 2000/2003 DNS. Windows Server 2008
R2 also incorporates IPv6 fully into the DNS and protocol stack to allow administrators to
deploy IPv6 immediately.
Whether using DNS for a full-fledged Active Directory Domain Services implementation or
simply setting up an Internet DNS presence, Windows Server 2008 R2’s DNS builds on a
successful, road-tested base to provide for a functional, reliable, enterprise name-resolu-
tion strategy.
ptg
The following are best practices from this chapter:
. Use Windows Server 2008 R2 DNS whenever possible to support Active Directory
Domain Services. If you must use a non-Windows DNS to host the AD zone, ensure
that it supports SRV records, such as with BIND version 8.1.2 or higher.
. Establish a caching-only server in small branch office situations to alleviate large
amounts of client query traffic across the network and to eliminate the need to repli-
cate entire DNS zones to remote locations.
. Configure DHCP to dynamically update DNS information for down-level clients if
dynamic records are necessary.
. Identify the sources of dynamically updated information to prevent problems with
reliability.
. Configure a DNS server to point to itself for DNS queries rather than to another
DNS server.
. Make any DNS implementation compliant with the standard DNS character set so
10
that you can support zone transfers to and from non-Unicode-compliant DNS imple-
mentations such as UNIX BIND servers. This includes a–z, A–Z, 0–9, and the hyphen
(-) character.
. Use the GlobalNames zone (GNZ) to reduce the reliance on WINS in the enterprise.
. Turn on Debug Logging on a per-server basis for more advanced DNS event log diagno-
sis only when required, and turn off this functionality when it’s no longer necessary.
. Begin to deploy IPv6 to gain familiarity with the new addressing.
This page intentionally left blank
ptg
IN THIS CHAPTER
DHCP/WINS/Domain
. Understanding the Key
Components of an Enterprise
Network
Controllers
. Exploring the Dynamic Host
Configuration Protocol (DHCP)
. Exploring DHCP Changes in
Windows Server 2008 R2
. Enhancing DHCP Reliability
Often, some of the more important components of a
network are overlooked because they consistently do their
. Implementing Redundant
job and keep a low profile. It’s only when a problem erupts
DHCP Services
with one of these components that their true value arises
. Exploring Advanced DHCP
and attention is paid to them. The Dynamic Host
Concepts
Configuration Protocol (DHCP) and the Windows Internet
Naming Service (WINS) are two such services, faithfully
. Securing DHCP
performing their functions day in and day out, while often
. Reviewing the Windows Internet
delegated to a beat-up old server.
Naming Service (WINS)
ptg
Although not glamorous, the functionality in DHCP and
. Installing and Configuring WINS
WINS is critical in a network environment, and a good deal
. Planning, Migrating, and
of thought should be put into their design, administration,
Maintaining WINS
and functional requirements. This chapter explores these
oft-forgotten services and provides best-practice design and
. Exploring Global Catalog
Domain Controller Placement
configuration information for utilizing them.
In addition to information on DHCP and WINS, this
chapter explores the functionality of global catalog domain
controllers in a Windows Server 2008 R2 Active Directory
infrastructure, specifically focusing on server placement
issues. In addition, a new type of domain controller released
with Windows Server 2008, Read-Only Domain Controller,
is explored. Finally, this chapter includes step-by-step instal-
lation instructions for these services and best-practice
migration scenarios.
326
CHAPTER 11
DHCP/WINS/Domain Controllers
Understanding the Key Components of an
Although an enterprise network has many functional layers, this chapter focuses on three
key concepts that are critical to the functionality of a Windows Server 2008 R2 environ-
ment. These three concepts—network addressing, name resolution, and directory integra-
tion—provide for the base-level functionality expected of any modern enterprise or even a
small business network, and they provide the backbone for the Windows Server 2008 R2
infrastructure.
Detailing the Importance of Network Addressing
The first concept of a network is network addressing. Network addressing allows for
systems to be attached to a network, and it lays the foundation to allow for communica-
tion between network systems. Network addressing was historically configured by propri-
etary network protocols, one for each network operating system (NOS). This gave NOS
designers a great deal of flexibility in tailoring the communications components of their
network to their specific design needs but made it difficult to exchange information
between networks or systems running different network operating systems.
ptg
One of the first common network protocols developed was the Transmission Control
Protocol/Internet Protocol (TCP/IP). TCP/IP was designed to interoperate between a differ-
ent variety of networks and network operating systems, allowing network clients to speak
a common language. The rise of this protocol coincided with the widespread adoption of
the Internet itself, and it was this popularity and ubiquitous use of this protocol that led
Microsoft to choose it as the standard protocol for Windows 2000. Windows Server 2008
R2 continues to use TCP/IP as the default network protocol, fortifying its position within
the Microsoft NOS world. And to be frank, any company that develops an operating
system that does not support TCP/IP or the next-generation version, IPv6, will never have
widespread adoption in the business or consumer computer, network, and Internet market.
TCP/IP requires that each node or device on the network be assigned a unique IP address,
such as 192.l68.206.10. One way to look at this is to consider that each computer IP
address is just like a phone number. Each household with a phone has a unique number,
but the neighbors may share a common area code and prefix. TCP/IP networking works
similarly in that each node’s IP address on a common network will share some common
number, called the network number, and the unique portion is called the host number.
Each node that is connected and desires to communicate on the network must be assigned
an IP address manually or by an automatic method. The automatic method is provided by
a service known as Dynamic Host Configuration Protocol or DHCP. Of course with DHCP,
proper planning and management of addresses and configuration options is essential and,
historically, many DHCP services lacked functionality. This is where the Windows Server
2008 R2 DHCP service really shines with new features that will enable better management
and higher reliability. You can find more details on DHCP in the “Exploring DHCP
Changes in Windows Server 2008 R2” section later in this chapter.
Understanding the Key Components of an Enterprise Network
327
Understanding Name Resolution
The second concept or desired function on a network is name resolution. Because humans
11
understand and remember names better than they do phone numbers, for example—or
for this chapter, IP addresses—the need for name resolution was realized early in the
development phases of computer networking. Name resolution can be described as match-
ing a name to an IP address for the purposes of establishing network communication.
Windows Server 2008 R2 provides two services that provide computer networking name
resolution. These two services are the domain name system (DNS) and the Windows
Internet Naming Service (WINS), which is detailed in this chapter.
The first type, the domain name system (DNS), translates fully qualified domain names
(FQDNs) into IP addresses, which allows them to be addressed in an Active Directory or
Internet DNS infrastructure. DNS name resolution is the standard for all Internet name
resolution and it is required in all Microsoft Active Directory environments. The DNS
service is covered in more detail in Chapter 10, “Domain Name System and IPv6.”
The second type of name resolution, mapping legacy Microsoft NetBIOS names into IP
addresses, is provided by WINS. Although it is technically possible (and ideal) to create a
Windows Server 2008 R2 environment free of NetBIOS name resolution, the truth is that
divorcing a network from WINS dependency is very difficult, so it will likely remain an
ptg
active part of network services in most organizations, at least for a few more years. You
can find more information on WINS in the “Reviewing the Windows Internet Naming
Service (WINS)” section later in this chapter.
NOTE
When Windows Server 2008 DNS service was released, it introduced a new feature,
known as the GlobalNames zone. The GlobalNames zone provided single-label name
resolution for large enterprise networks that do not deploy WINS and for which using
DNS name suffixes to provide single-label name resolution was not practical. See