The Code Book (23 page)
Figure 32
Captain Midnight’s Code-o-Graph, which enciphers each plaintext letter (outer disk) as a number (inner disk), rather than a letter.
The important feature of using the cipher disk in this way is the fact that the disk is changing its mode of scrambling during encryption. Although this extra level of complication makes the cipher harder to break, it does not make it unbreakable, because we are simply dealing with a mechanized version of the Vigenère cipher, and the Vigenère cipher was broken by Babbage and Kasiski. However, five hundred years after Alberti, a more complex reincarnation of his cipher disk would lead to a new generation of ciphers, an order of magnitude more difficult to crack than anything previously used.
In 1918, the German inventor Arthur Scherbius and his close friend Richard Ritter founded the company of Scherbius & Ritter, an innovative engineering firm that dabbled in everything from turbines to heated pillows. Scherbius was in charge of research and development, and was constantly looking for new opportunities. One of his pet projects was to replace the inadequate systems of cryptography used in the First World War by swapping pencil-and-paper ciphers with a form of encryption that exploited twentieth-century technology. Having studied electrical engineering in Hanover and Munich, he developed a piece of cryptographic machinery that was essentially an electrical version of Alberti’s cipher disk. Called Enigma, Scherbius’s invention would become the most fearsome system of encryption in history.
Scherbius’s Enigma machine consisted of a number of ingenious components, which he combined into a formidable and intricate cipher machine. However, if we break the machine down into its constituent parts and rebuild it in stages, then its underlying principles will become apparent. The basic form of Scherbius’s invention consists of three elements connected by wires: a keyboard for inputting each plaintext letter, a scrambling unit that encrypts each plaintext letter into a corresponding ciphertext letter, and a display board consisting of various lamps for indicating the ciphertext letter.
Figure 33
shows a stylized layout of the machine, limited to a six-letter alphabet for simplicity. In order to encrypt a plaintext letter, the operator presses the appropriate plaintext letter on the keyboard, which sends an electric pulse through the central scrambling unit and out the other side, where it illuminates the corresponding ciphertext letter on the lampboard.
The scrambler, a thick rubber disk riddled with wires, is the most important part of the machine. From the keyboard, the wires enter the scrambler at six points, and then make a series of twists and turns within the scrambler before emerging at six points on the other side. The internal wirings of the scrambler determine how the plaintext letters will be encrypted. For example, in
Figure 33
the wirings dictate that:
typing in a will illuminate the letter B, which means that a is encrypted as B,
typing in b will illuminate the letter A, which means that b is encrypted as A,
typing in c will illuminate the letter D, which means that c is encrypted as D,
typing in d will illuminate the letter F, which means that d is encrypted as F,
typing in e will illuminate the letter E, which means that e is encrypted as E,
typing in f will illuminate the letter C, which means that f is encrypted as C.
The message cafe would be encrypted as DBCE. With this basic setup, the scrambler essentially defines a cipher alphabet, and the machine can be used to implement a simple monoalphabetic substitution cipher.
However, Scherbius’s idea was for the scrambler disk to automatically rotate by one-sixth of a revolution each time a letter is encrypted (or one-twenty-sixth of a revolution for a complete alphabet of 26 letters).
Figure 34(a)
shows the same arrangement as in
Figure 33
; once again, typing in the letter b will illuminate the letter A. However, this time, immediately after typing a letter and illuminating the lampboard, the scrambler revolves by one-sixth of a revolution to the position shown in
Figure 34(b)
. Typing in the letter b again will now illuminate a different letter, namely C. Immediately afterward, the scrambler rotates once more, to the position shown in
Figure 34(c)
. This time, typing in the letter b will illuminate E. Typing the letter b six times in a row would generate the ciphertext ACEBDC. In other words, the cipher alphabet changes after each encryption, and the encryption of the letter b is constantly changing. With this rotating setup, the scrambler essentially defines six cipher alphabets, and the machine can be used to implement a polyalphabetic cipher.
The rotation of the scrambler is the most important feature of Scherbius’s design. However, as it stands the machine suffers from one obvious weakness. Typing b six times will return the scrambler to its original position, and typing b again and again will repeat the pattern of encryption. In general, cryptographers are keen to avoid repetition because it leads to regularity and structure in the ciphertext, symptoms of a weak cipher. This problem can be alleviated by introducing a second scrambler disk.
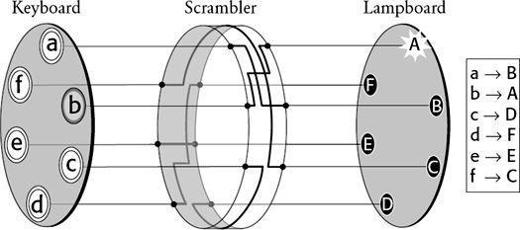
Figure 33
A simplified version of the Enigma machine with an alphabet of just six letters. The most important element of the machine is the scrambler. By typing in b on the keyboard, a current passes into the scrambler, follows the path of the internal wiring, and then emerges so as illuminate the A lamp. In short, b is encrypted as A. The box to the right indicates how each of the six letters is encrypted.
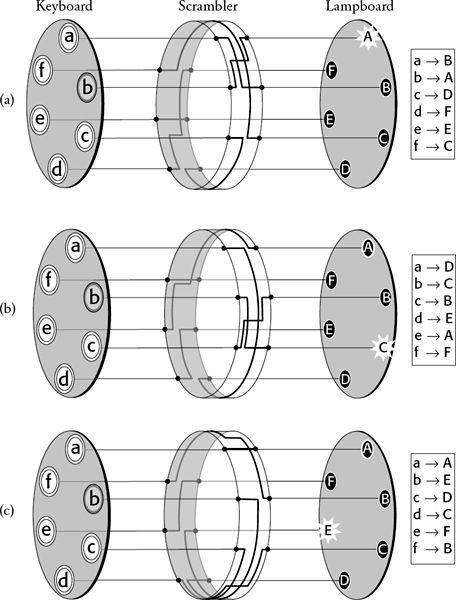
Figure 34
Every time a letter is typed into the keyboard and encrypted, the scrambler rotates by one place, thus changing how each letter is potentially encrypted. In (a) the scrambler encrypts b as A, but in (b) the new scrambler orientation encrypts b as C. In (c), after rotating one more place, the scrambler encrypts b as E. After encrypting four more letters, and rotating four more places, the scrambler returns to its original orientation.
Figure 35
is a schematic of a cipher machine with two scramblers. Because of the difficulty of drawing a three-dimensional scrambler with three-dimensional internal wirings,
Figure 35
shows only a two-dimensional representation. Each time a letter is encrypted, the first scrambler rotates by one space, or in terms of the two-dimensional diagram, each wiring shifts down one place. In contrast, the second scrambler disk remains stationary for most of the time. It moves only after the first scrambler has made a complete revolution. The first scrambler is fitted with a tooth, and it is only when this tooth reaches a certain point that it knocks the second scrambler on one place.
In
Figure 35(a)
, the first scrambler is in a position where it is just about to knock forward the second scrambler. Typing in and encrypting a letter moves the mechanism to the configuration shown in
Figure 35(b)
, in which the first scrambler has moved on one place, and the second scrambler has also been knocked on one place. Typing in and encrypting another letter again moves the first scrambler on one place,
Figure 35(c)
, but this time the second scrambler has remained stationary. The second scrambler will not move again until the first scrambler completes one revolution, which will take another five encryptions. This arrangement is similar to a car odometer—the rotor representing single miles turns quite quickly, and when it completes one revolution by reaching “9,” it knocks the rotor representing tens of miles forward one place.
The advantage of adding a second scrambler is that the pattern of encryption is not repeated until the second scrambler is back where it started, which requires six complete revolutions of the first scrambler, or the encryption of 6 × 6, or 36 letters in total. In other words, there are 36 distinct scrambler settings, which is equivalent to switching between 36 cipher alphabets. With a full alphabet of 26 letters, the cipher machine would switch between 26 × 26, or 676 cipher alphabets. So by combining scramblers (sometimes called rotors), it is possible to build an encryption machine which is continually switching between different cipher alphabets. The operator types in a particular letter and, depending on the scrambler arrangement, it can be encrypted according to any one of hundreds of cipher alphabets. Then the scrambler arrangement changes, so that when the next letter is typed into the machine it is encrypted according to a different cipher alphabet. Furthermore, all of this is done with great efficiency and accuracy, thanks to the automatic movement of scramblers and the speed of electricity.
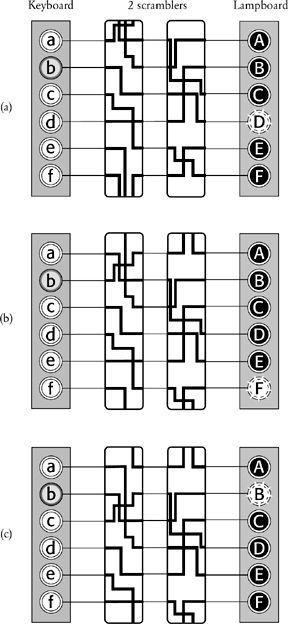
Figure 35
On adding a second scrambler, the pattern of encryption does not repeat until 36 letters have been enciphered, at which point both scramblers have returned to their original positions. To simplify the diagram, the scramblers are represented in just two dimensions; instead of rotating one place, the wirings move down one place. If a wire appears to leave the top or bottom of a scrambler, its path can be followed by continuing from the corresponding wire at the bottom or top of the same scrambler. In (a), b is encrypted as D. After encryption, the first scrambler rotates by one place, also nudging the second scrambler around one place—this happens only once during each complete revolution of the first wheel. This new setting is shown in (b), in which b is encrypted as F. After encryption, the first scrambler rotates by one place, but this time the second scrambler remains fixed. This new setting is shown in (c), in which b is encrypted as B.
Before explaining in detail how Scherbius intended his encryption machine to be used, it is necessary to describe two more elements of the Enigma, which are shown in
Figure 36
. First, Scherbius’s standard encryption machine employed a third scrambler for extra complexity—for a full alphabet these three scramblers would provide 26 × 26 × 26, or 17,576 distinct scrambler arrangements. Second, Scherbius added a
reflector
. The reflector is a bit like a scrambler, inasmuch as it is a rubber disk with internal wirings, but it differs because it does not rotate, and the wires enter on one side and then reemerge on the same side. With the reflector in place, the operator types in a letter, which sends an electrical signal through the three scramblers. When the reflector receives the incoming signal it sends it back through the same three scramblers, but along a different route. For example, with the setup in
Figure 36
, typing the letter b would send a signal through the three scramblers and into the reflector, whereupon the signal would return back through the wirings to arrive at the letter D. The signal does not actually emerge through the keyboard, as it might seem from
Figure 36
, but instead is diverted to the lampboard. At first sight the reflector seems to be a pointless addition to the machine, because its static nature means that it does not add to the number of cipher alphabets. However, its benefits become clear when we see how the machine was actually used to encrypt and decrypt a message.