Windows Server 2008 R2 Unleashed (12 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto
Policy Management.”
NOTE
When running the Group Policy Management Console to manage a Windows Server
2008 R2 Active Directory environment, run the GPMC tool from a Windows Server 2008
R2 server or a Windows 7 client system to have access to all the editable objects avail-
able. If you run the GPMC tool from a Windows 2003 server or Windows XP client, you
will not see all the features nor have full access to edit all objects available.
This is because Windows Server 2008 R2 now supports new template file formats
(ADMX and ADML) that are only accessible from Windows Server 2008, Windows
Server 2008 R2, Windows Vista, and Windows 7 systems.
24
CHAPTER 1
Windows Server 2008 R2 Technology Primer
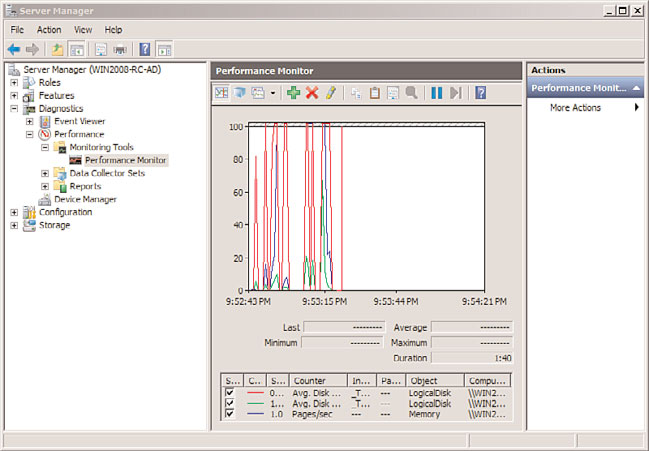
Introducing Performance and Reliability Monitoring Tools
Windows Server 2008 R2 introduces new and revised performance and reliability monitor-
ing tools intended to help network administrators better understand the health and opera-
tions of Windows Server 2008 R2 systems. Just like with the Group Policy Management
Console, the new Reliability and Performance Monitor shows up as a feature in the Server
Manager console. By clicking on the Performance Diagnostic Console, the tool shows up
in the right pane, as shown in Figure 1.8.
ptg
FIGURE 1.8
Windows Reliability and Performance Monitor.
The new tool keeps track of system activity and resource usage and displays key counters
and system status on screen. The Reliability Monitor diagnoses potential causes of server
instability by noting the last time a server was rebooted, what patches or updates were
applied, and chronologically when services have failed on the system so that system faults
can potentially be traced back to specific system updates or changes that occurred prior to
the problem.
By combining what used to be three to four tools into a single console, administrators are
able to look at system performance, operational tasks, and historical event information in
their analysis of a server problem or system operations instability. You can find more
details on performance and reliability monitoring in Chapter 34.
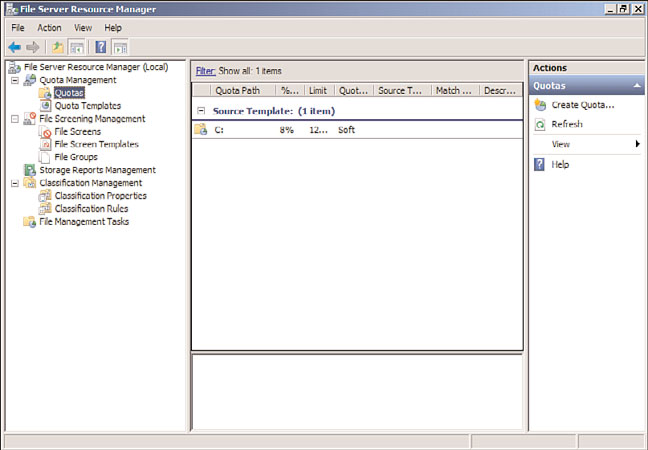
Leveraging File Server Resource Manager
File Server Resource Manager (FSRM) was a feature pack add-in to Windows 2003 R2 and
has been significantly improved with the release of Windows Server 2008 R2. FSRM is a
quota management system of files on network shares across an enterprise. Rather than
Windows Server 2008 R2 Benefits for Administration
25
allowing employees to copy the entire content of their laptop to a network, or potentially
back up their MP3 audio files onto a network, FSRM provides the ability to not only limit
1
the amount of content stored on network shares, but also to set quotas (or limit storage
altogether) on certain file types. So, a user could be limited to store 200GB of files on a
network share, but of that limit, only 2GB can be allocated to MP3 files.
FSRM, shown in Figure 1.9, in Windows Server 2008 R2 has been improved to allow the
nesting of quotas to ensure the most restrictive policy is applied. Quotas can also tran-
scend subfolders, so as new folders are created, or as policies are applied at different levels
in a folder hierarchy, the policies still apply, and the rules are combined to provide
varying levels of quota allocation to user data. Additionally, quotas are now based on
actual storage, so if a file is compressed when stored, the user will be able to store more
files within their allocated quota.
ptg
FIGURE 1.9
File Server Resource Manager.
File Server Resource Manager is covered in detail in Chapter 28.
Leveraging the Best Practice Analyzer
Included in Windows Server 2008 R2 is a built-in Best Practice Analyzer. Found in the
Server Manager console tool, the Best Practice Analyzer runs a series of tests against Active
Directory roles, such as the Hyper-V role, the DNS role, and the Remote Desktop Services
role, to assess whether the role has been installed and configured properly and to compare
the installation with tested best practices.
26
CHAPTER 1
Windows Server 2008 R2 Technology Primer
Some of the results from the Best Practice Analyzer could tell an administrator they need
to add more memory to a server, to move a role to a separate server to improve role opti-
mization, or to shift a database to a different drive on the server to distribute disk perfor-
mance demands on the system. More details on the Best Practice Analyzer are covered in
Chapter 20.
Introduction of Windows Deployment Services
Windows Server 2008 introduced a new tool called Windows Deployment Services (WDS),
which was effectively an updated version of the Remote Installation Services (RIS) that has
been available for the past several years. Unlike RIS, which was focused on primarily
scripted installations and client images, WDS in Windows Server 2008 R2 can distribute
images of Windows 7 clients or Windows Server 2008 R2 servers in a significantly more
flexible and modifiable deployment process.
Like with RIS, Windows Deployment Services allows a client system to initiate a Preboot
Execution Environment (PXE), effectively “booting” to the WDS server to see a list of
images that can be deployed on the system. Alternately, an organization can create a
Windows PE boot disc and have an image initiated from a CD or DVD.
With Windows Server 2008 R2 and Windows 7, the image can be created in Windows
Imaging (WIM) format, which allows for the injection of patches, updates, or even new
ptg
code to a WIM file without even booting the image file. This provides the organization
with more than just static images that get pushed out like in RIS, but rather a tool that
provides ongoing and manageable updates to image files.
WDS also supports the imaging of Windows 2003 servers and Windows XP client systems
in the same manner that RIS did in terms of pushing out images or using an unattend
script file to send images to systems.
Windows Deployment Services is covered in detail in Chapter 26, “Windows Server 2008
R2 Administration Tools for Desktops.”
Improvements in Security in Windows Server 2008 R2
Significantly more than just cosmetic updates are the security enhancements added to
Windows Server 2008 R2. As organizations are struggling to ensure that their environ-
ments are secure, employees can depend on information privacy, and content is protected
for regulatory compliance reasons; having the tools to secure the environment is critical.
Enhancing the Windows Server 2008 R2 Security Subsystem
Part IV of this book, “Security,” is focused on security in the different core areas. Chapter
13 addresses core security subsystems of Windows Server 2008 R2 as it relates to server
systems. This includes the basics of server hardening, patching, and updating but also
extends into new server security areas added to Windows Server 2008 R2, such as device
control level security, wireless access security, and Active Directory Rights Management
Services (RMS). Windows Server 2008 R2 has continued the “secure by default” theme at
Improvements in Security in Windows Server 2008 R2
27
Microsoft and no longer installs components like Internet Information Services (IIS) by
default. The good part about it is that components that are not core to the operation of a
1
server are not installed on the system; however, it means every time you install software,
you need to add basic components and features. Getting to remember what has to be
installed, configured, or made operational is important as servers are being built and
added to a Windows Active Directory environment.
Transport Security Using IPSec and Certificate Services
Chapter 14, “Transport-Level Security,” addresses site-to-site and server-to-server security,
addressed through the implementation of IPSec encryption. Not new to Windows, IPSec
has finally gotten several new Group Policy management components added to aid in the
implementation and management of IPSec in the enterprise. Also not new to Windows,
but something that has been greatly enhanced, is Microsoft’s offering around Public Key
Infrastructure (PKI), specifically Certificate Services. It seems like everything security
related is somehow connected to certificates, whether that is file encryption using
Encrypting File System (EFS), email encryption using S/MIME, remote mobile device
synchronization using certificate access, or transport security using IPSec. Everything
needs a certificate, and the ability of an organization to easily create and manage certifi-
cates is the focus of Chapter 14.
ptg
Security Policies, Policy Management, and Supporting Tools for
Policy Enforcement
Completely new to Windows Server 2008, updated in Windows Server 2008 R2, and a
major focus for organizations are security policies and policy management around security
systems. It used to be we would just lock down systems, make sure they were secure by
default, and use our best judgment and best effort to secure a network. However, with
laws and regulations, or even human resource departments getting involved in informa-
tion security, the root of all IT security practices fall on having set security policies defined
so that IT can implement technologies to address the organization policies around infor-
mation security. This is covered in detail in Chapter 15, “Security Policies, Network Policy
Server, and Network Access Protection.”
Chapter 15 goes beyond the policies and common best practices around policy manage-
ment in an enterprise, and also digs into the underlying technologies that help organiza-
tions turn security policies into IT-managed technology services. Tools like the Network
Policy Server in Windows Server 2008 R2 allow policies to be defined, and the Network
Policy Server enforces those policies, specifically around remote logon access, access over
wireless network connections, or the integration of Network Access Protection (NAP) in
querying a device and making sure the device (desktop, laptop, or mobile device) has the
latest patches, updates, and antivirus software dictated by management to ensure a
device is secure.
28
CHAPTER 1
Windows Server 2008 R2 Technology Primer
Improvements in Mobile Computing in Windows
As organizations find their workforce becoming more and more mobile, Microsoft has
made significant improvements to mobility in Windows Server 2008 R2. New technologies
provide a more seamless experience for users with laptops to move from office, to home,
to Internet Wi-Fi hot spots and maintain connectivity to network resources. These
improvements do require mobile users to run the latest Windows 7 client operating
system on their laptop system to gain access to these new services; however, once imple-
mented, users find the functionality to greatly support easier access to network resources
no matter where the user resides.
Windows Server 2008 R2 DirectAccess
One of the significant remote access enhancements in Windows Server 2008 R2 is the
DirectAccess technology. DirectAccess provides a remote user the ability to access network
resources such as file shares, SharePoint shares, and the like without having to launch a