Windows Server 2008 R2 Unleashed (85 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto
selected when you want to provide public access to an FTP site without having end
users pass credentials.
12
.
Basic Authentication—
It is another built-in authentication mechanism for FTP
sites. Basic authentication requires the FTP clients to enter a valid Windows user
account and password when gaining access to the FTP site. Basic Authentication
sends password credentials in clear text, which is a security hazard. As such, imple-
ment SSL when using this mechanism to encrypt passwords in transit.
.
ASP.NET Authentication—
The FTP site will provide authorization to FTP clients by
having them enter a valid ASP.NET user account and password. This is a custom
authentication mechanism that requires a provider and connection string to an
ASP.NET user database.
.
IIS Manager Authentication—
This is another custom authentication mechanism
similar to ASP.NET. An FTP client must provide a legitimate IIS Manager username
and password to gain access to FTP content. Similar to Basic Authentication, the cre-
dentials are not encrypted, so it is recommended for this authentication to be used
ptg
in conjunction with SSL.
NOTE
Don’t forget that to utilize these authentication mechanisms, the appropriate authenti-
cation role services must be installed prior to configuration.
FTP Authorization Rules Feature Page
This page should be used to manage Allow and Deny authorization rules that control
access to FTP sites. The Actions pane options Add Allow Rule and Add Deny Rule should
be selected to invoke the Allow or Deny Authorization Rule page. After the page is
invoked, rules can be applied to All Users, All Anonymous Users, Specified Roles or User
Groups, and Specified Users. In addition, the rules are based on Read or Write permissions.
FTP Current Sessions Feature Page
This page should be used to monitor current sessions for an FTP site. The following
elements are displayed: User Name, Session Start Time, Current Command, Previous
Command, Command Start Time, Bytes Sent, Bytes Received, Session ID, and Client IP.
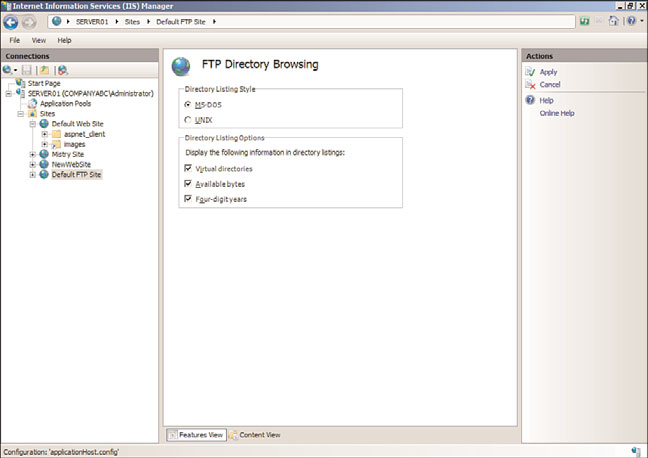
FTP Directory Browsing Feature Page
The FTP Directory Browsing page illustrated in Figure 12.13 is broken out into two
sections. The first section is called Directory Listing Style. The format presentation options
404
CHAPTER 12
Internet Information Services
FIGURE 12.13
The FTP Directory Browsing feature page.
ptg
include MS-DOS and UNIX. The second section, Directory Listing Options, controls how
directory information is displayed. The display options include the following:
.
Virtual Directories—
This option allows you to specify whether to include virtual
directories.
.
Available Bytes—
This setting controls the display behavior of the available bytes
remaining when a disk quota is enabled.
.
Four-Digit Years—
When enabled, this setting displays the last modified date for a
file based on the four-year date, such as 1974, and not a two-year date format, such
as 74.
FTP Firewall Support Feature Page
A new FTP feature associated with IIS 7.5 is the FTP Firewall Support. This feature allows
the server to accept passive connections when the FTP client is behind a firewall. An
administrator must enter the Data Channel Port Range and External IP Address of the
Firewall settings and then click Apply in the Actions pane.
FTP IPv4 and Domain Restrictions Feature Page
The exact same settings are associated with the FTP IPv4 and Domain Restrictions as for a
website in IIS 7.5. The FTP IPv4 and Domain Restrictions feature page should be used to
create and manage rules that allow computer networks and IP addresses the opportunity
to either gain access or be denied to specific web content. You can either allow or deny
access. It is also possible to enter a single IP address, a range of IP addresses, or a domain
name. Finally, rules can be added to a page, site, or inherited from the parent.
Installing and Configuring FTP Services
405
FTP Logging Feature Page
The FTP Logging feature page includes the exact same logging settings as for a website.
This page controls the type of log file to use, the location to be stored, and the log file
rollover settings.
12
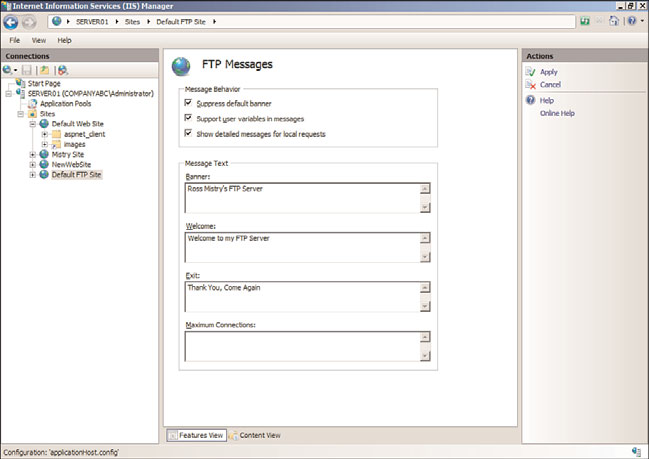
FTP Messages Feature Page
The FTP Messages feature page illustrated in Figure 12.14 is a great way to create a banner,
or welcome and exit message that will be displayed to FTP users. The message behavior is
controlled by the following elements:
.
Suppress Default Banner—
If enabled, this option displays a default welcome
banner. Otherwise, a customizable banner is displayed.
.
Support User Variables in Messages—
By enabling this setting, user variables such
as BytesReceived, BytesSent, SessionID, SiteName, and UserName are included in the
message banner.
.
Show Detailed Messages for Local Requests—
This setting controls the behavior
for displaying FTP error messages. If enabled, FTP error messages are displayed to the
local host.
ptg
The next section on the FTP Messages feature page is called Message Text. The administra-
tor enters message text in the various text boxes. The message boxes include Banner,
Welcome, Exit, and Maximum Connections.
FIGURE 12.14
The FTP Messages feature page.
406
CHAPTER 12
Internet Information Services
FTP Request Filtering
The FTP Request Filtering feature page should be used to define the list of Allow or Deny
rules based on the specific elements:
.
File Name Extensions—
This tab allows for the creation of filename extensions for
which the FTP service will either allow or deny access to the site. For example, an
administrator can prevent Internet clients from uploading any files with the exten-
sion of *.txt or *.com.
.
Hidden Segments—
The Hidden Segments tab should be used if you want to hide
specific areas of your FTP site. If hidden, the specific section will not be displayed in
the directory listings.
.
Defined URL Sequences—
This setting should be used to define the list of URL
sequences for which the FTP service will deny access.
.
Commands—
The final tab Commands defines the list of commands for which the
FTP service will either allow or deny access to further tighten security.
FTP SSL Settings Feature Page
This page should be utilized for enabling and configuring SSL settings for an FTP site. The
options include a drop-down menu for selecting the SSL certificate you will use and SSL
ptg
policy. The SSL Policy options include Allow SSL Connections, Require SSL Connections,
and Advanced Custom Settings. You will also have the chance to choose whether to use
128-bit encryption for SSL connections.
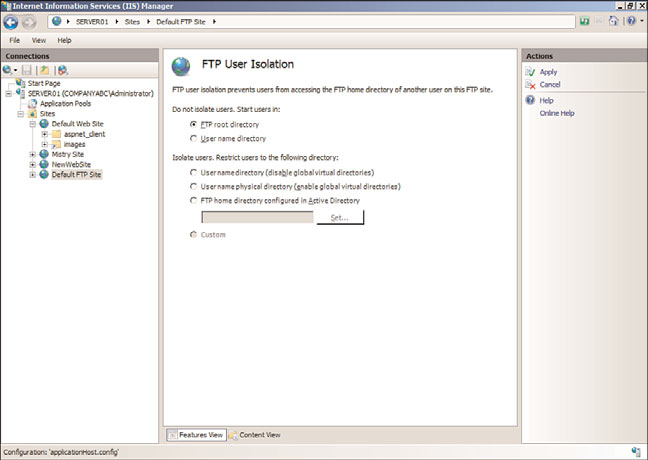
FTP User Isolation Feature Page
Similar to IIS 6.0, IIS 7.5 can still isolate FTP users so FTP content is protected. This is an
especially useful feature for Internet service providers (ISPs) and application service
providers (ASPs) servicing a large number of users. FTP users can have their own separate
directory to upload and download files to the web or FTP server. Users who connect see only
their directory as the top-level directory and can’t browse other FTP directories. Permissions
can be set on the FTP home directory to allow create, modify, or delete operations.
It is worth noting that FTP user isolation is based on an FTP site rather than at the server
level and is either enabled or disabled. However, sites that need to enable FTP user isola-
tion aren’t forced to strictly use this feature. You can enable anonymous access in
conjunction with FTP user isolation by creating a virtual directory within the FTP site and
allowing read-only access. The only limitation to mixing the FTP user isolation and
anonymous access is that information can be downloaded only from the public or read-
only virtual directory.
The configuration settings on the FTP User Isolation page, as shown in Figure 12.15,
consist of the following options for where to start the user when they connect. The
options include the FTP Root Directory or User Name Directory. In addition, it is possible
Securing Internet Information Services 7.5
407
12
FIGURE 12.15
The FTP User Isolation feature page.
ptg
to isolate users by restricting them to following directories. The Isolate Users options
consist of the following:
. User Name Directory (Disable Global Virtual Directories)
. User Name Physical Directory (Enable Global Virtual Directories)
. FTP Home Directory Configured in Active Directory
Securing Internet Information Services 7.5
There shouldn’t be any question that IIS is significantly more secure than its predecessors.
Several key enhancements such as a reduced attack surface, minimum install by default,
and enhanced application isolation deliver a robust and secure web platform. IIS also is
enabled by default to present only static information (that is, to use applications or other
dynamic content, you must manually enable them).
However, Microsoft products are also the most popular products to try to hack. For this
reason, it’s important to secure the web server as much as possible. The more barriers there
are, the less inclined a hacker would be to try to gain unauthorized access. Each compo-
nent on the web server must be secure; the server is only as secure as its weakest point.
408
CHAPTER 12
Internet Information Services
Windows Server 2008 R2 Security
Windows Server 2008 R2 security actually begins during the planning and designing
phases so that every conceivable security aspect is addressed. This can entail physical,
logical (Windows Server 2008 R2, applications, and so on), and communications security.
When you’re securing the Windows Server 2008 R2 system with the Web Server role, it’s
important to use NTFS on the disk subsystem and apply the latest service pack and secu-
rity patches. Using NTFS is critical because it can have appropriate permissions set on files,
folders, and shares. Also, keeping up to date with service packs and patches ensures that
Windows Server 2008 R2 is operating with the greatest amount of protection.
Application security on the Windows Server 2008 R2 system with the Web Server role