Windows Server 2008 R2 Unleashed (89 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto
vidual can simply pull up in the parking lot and access an organization’s local area
network (LAN) via a laptop computer and a standard wireless card. The standard security
employed by wireless networks, Wireless Encryption Protocol (WEP), is effectively worth-
less because it can be cracked in several minutes.
Controlling the network ports and securing network switches are part of the securing
strategy. For organizations with wireless networks, more stringent precautions must be
taken. Deployment of wireless networks using the 802.1x protocol vastly increases the
security of the mechanism. Microsoft uses 802.1x to secure its vast wireless network, and
Windows Server 2008 R2 fully supports the protocol.
For those organizations without the time or resources to deploy 802.1x, the simple step of
placing wireless access points outside the firewall and requiring virtual private network
ptg
(VPN) access through the firewall can effectively secure the wireless network. Even if tres-
passers were to break the WEP key, they would be connected only to an orphaned
network, with no place to go.
Firewall Security
Deployment of an enterprise firewall configuration is a must in any environment that is
connected to the Internet. Servers or workstations directly connected to the Internet are
prime candidates for hacking. Modern firewall implementations such as Microsoft’s Internet
Security and Acceleration (ISA) 2006 offer advanced configurations, such as web proxying
and demilitarized zone (DMZ) configuration, as well. Proper setup and configuration of a
firewall in between a Windows Server 2008 R2 network and the Internet are a must.
Using the Integrated Windows Firewall with
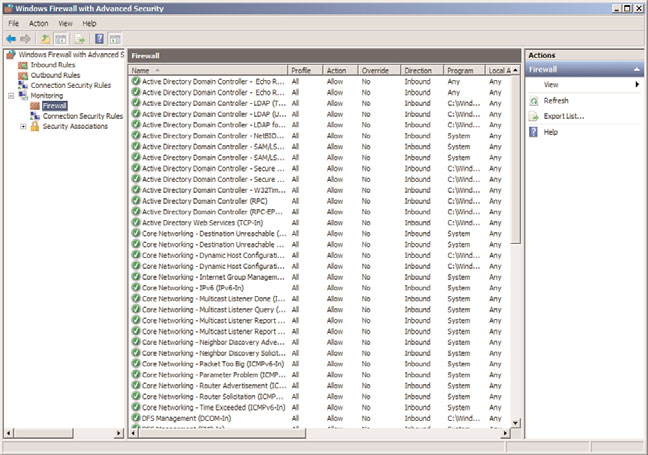
Windows Server 2008 R2 includes a vastly improved integrated firewall that is turned on
by default in all installations of the product. The firewall, administered from an MMC
snap-in shown in Figure 13.3 (Start, All Programs, Administrative Tools, Windows Firewall
with Advanced Security), gives unprecedented control and security to a server.
Understanding Windows Firewall Integration with Server Manager
The firewall with advanced security is fully integrated with the Server Manager utility and
the Server Roles Wizard. For example, if an administrator runs the Server Roles Wizard and
chooses to make the server a file server, only then are those ports and protocols that are
required for file server access opened on the server.
Using the Integrated Windows Firewall with Advanced Security
425
13
FIGURE 13.3
Using the integrated Windows Firewall with Advanced Security.
ptg
NOTE
It is instinctual for most administrators to disable software firewalls on servers, as they
have caused problems with functionality in the past. This is not recommended in
Windows Server 2008 R2, however, as the product itself is tightly integrated with its
firewall, and the firewall itself provides for a much greater degree of security than previ-
ous versions of Windows Server provided.
Creating Inbound and Outbound Rules on the Windows Firewall
In certain cases, when a third-party application is not integrated with Server Manager, or
when needing to open specific individual ports, it might become necessary to create fire-
wall rules for individual services to run properly. Both inbound rules, addressing traffic to
the server, and outbound rules, addressing how the server can communicate out, can be
created. Rules can be created based on the following factors:
.
Program—
A rule can be created that allows a specific program executable access.
For example, you can specify that the c:\Program Files\Custom Program\mypro-
gram.exe file has full outbound access when running. The Windows Firewall
program will then allow any type of connections made by that program full access.
This can be useful in scenarios when a specific application server uses multiple
varied ports, but the overall security that the firewall provides is still desired.
426
CHAPTER 13
Server-Level Security
.
Port—
Entering a traditional UDP or TCP port into the Add Rules Wizard is
supported. This covers traditional scenarios such as “We need to open Port 8787 on
the server.”
.
Predefined—
Windows Server also has built-in, predefined rules, such as those that
allow AD DS, DFS, BITS, HTTP, and many more. The advantage to using a predefined
rule is that Microsoft has done all the legwork in advance, and it becomes much
easier to allow a specific service.
.
Custom—
The creation of custom rule types not covered in the other categories is
also supported.
For example, the following procedure details the creation of an inbound rule to allow a
custom application to use TCP Port 8787 for inbound communication:
1. Open the Windows Firewall MMC (Start, All Programs, Administrative Tools,
Windows Firewall with Advanced Security).
2. Click on the Inbound Rules node in the node pane.
3. In the Actions pane, click the New Rule link.
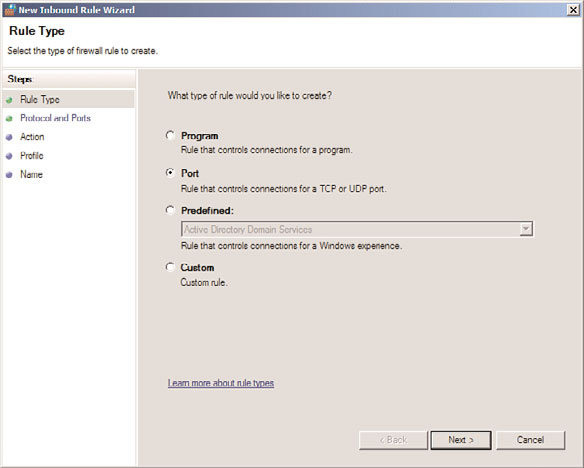
4. On the Rule Type page of the New Inbound Rule Wizard, shown in Figure 13.4,
select Port to create a rule based on the port, and click Next to continue.
ptg
FIGURE 13.4
Creating a rule on the Windows Firewall.
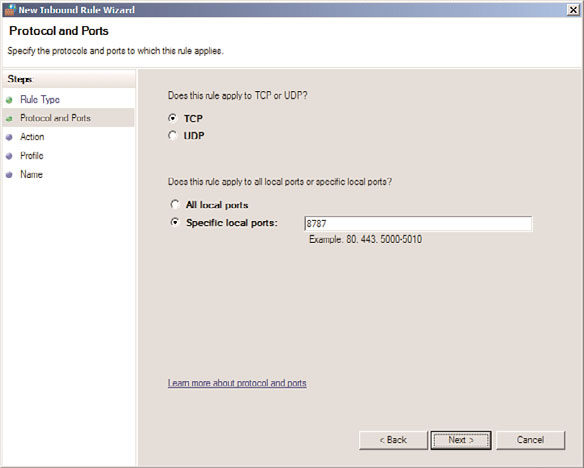
5. On the Protocol and Ports page, shown in Figure 13.5, select TCP, and enter 8787 in
the Specific Local Ports field. Click Next to continue.
6. On the Action page, select Allow to enable the connection.
Hardening Server Security
427
13
FIGURE 13.5
Entering port information for the firewall rule.
ptg
NOTE
The Action page of the New Inbound Rule Wizard also allows for a rule to be configured
that only allows the connection if it is secured using IPSec technologies. For more on
IPSec, see Chapter 14, “Transport-Level Security.”
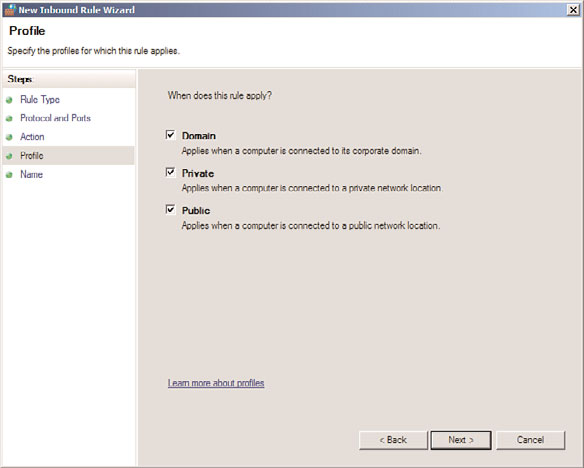
7. On the Profile page, shown in Figure 13.6, select all three check boxes. This enables
an administrator to specify that a rule only applies when connected to specific
networks. Click Next to continue.
8. Enter a descriptive name for the rule, and click Finish.
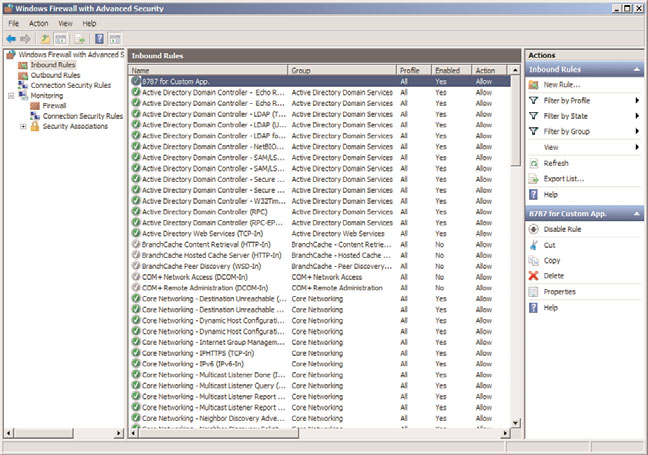
Review the rule settings in the Inbound Rules node, shown in Figure 13.7. This allows for
a quick-glance view of the rule settings. You can also include a rule in a rule group, which
allows for multiple rules to be tied together for easy on/off application.
Using the integrated Windows Firewall is no longer just a good idea; it’s a vital part of the
security of the product. The addition of the ability to define rules based on factors such as
scope, profile, IPSec status, and the like further positions the Server OS as one with high
levels of integrated security.
Previous versions of Windows Server required a great deal of configuration after installa-
tion to “harden” the security of the server and ensure that viruses and exploits would not
overwhelm or disable the server. The good news with Windows Server 2008 R2 is that, by
428
CHAPTER 13
Server-Level Security
FIGURE 13.6
Specifying the profile of a firewall rule.
ptg
FIGURE 13.7
Viewing the firewall rules.
Examining File-Level Security
429
default, many less commonly used services are turned off. In fact, a fresh installation of
Windows Server 2008 R2 only has those services enabled that are vital for the OS to run
properly, and everything else must be enabled by running Server Manager. In addition, by
default an intelligent firewall is enabled, and only those services that absolutely need to
run are allowed through the firewall.
Subsequently, in Windows Server 2008 R2, it is important to first define which roles a
server will utilize and then to turn on only those services that are necessary, with the use
of Server Manager, which automates the deployment of server roles.
13
Defining Server Roles
Depending on the size of an organization, a server might be designated for one or multi-
ple network roles. In an ideal world, a separate server or servers would be designated to
handle a single role, such as DHCP server or DNS server. Even smaller organizations can
take advantage of virtualization technology such as Windows Server 2008 R2’s Hyper-V
server virtualization platform to provision multiple dedicated guests on a smaller number
of physical hosts.
Because any service that is activated increases the overall risk, it is important to fully
define which roles a server will take on so that those services can be properly configured.